Security and Privacy: Living in a vulnerable, connected world
August 21, 2014

This is the fourth report in the Connected World Market Insights Series.
The size of the Internet of Things
A Raspberry Pi Model B+ Board costs $38.15 plus taxes and shipping. These credit card–size computers can be connected to a PC; they are designed for people who want to learn programming. The Raspberry Pi is also capable of interacting with the outside world (that is, the physical world) through a general-purpose input/output (GPIO), a pin that enables the board to be interfaced with sensors, motors and a plethora of other electronic devices. Why are we talking about Raspberry Pi? Because you could use one to prototype your next Internet of Things (IoT) project.
As seen on YouTube and Vimeo, thousands of “makers” (also known as hobbyists)—those who build new things, often electronic devices—are building new IoT products. These products include step-activated keyboards, DIY air-quality sensors, heart-rate monitors, and ambient light for all your gaming needs.
Sensors, wireless technologies and microprocessors (like the Raspberry Pi) are available for very low prices. Slowly, connectivity is being commoditized as well. The ingredients needed to build the hardware of the IoT are mostly accessible.
According to the research company Forrester, networks are also expanding. “Various types of networks, including wire lines, cellular wireless networks, licensed radio networks, and satellite solutions, enable IoT solutions and many telecom service providers have deployed IP networks at a national and international level; combined with the ubiquitous availability of 3G wireless networks in mature markets, these make IoT solution deployment possible.”1
Most makers and hobbyists creating IoT products at home will not become the future companies of a connected world. However, by trying different components and experimenting with technologies, they will help create and develop the type of products and business cases that will constitute the essence of IoT.
Slowly, the dreams of science fiction writers and hobbyists all around the world seems to be becoming reality. Gartner predicts that the IoT will consist of 26 billion installed units by 2020.2
Hacking refrigerators: The perceived security challenges of the IoT
Conceptually, the Internet was not designed to isolate information, but to connect it and make it available—as a result, we live in a world of constant security threats and cyber attacks. In that sense, the IoT is no different from other types of online activities. It is to be expected that, with the vast number of devices that will be connecting to the Internet in the coming years, the vulnerabilities of digital communication (already exploited to attack networks or steal personal information) will only increase.
According to a recent estimate by the Centre for Strategic and International Studies cited in the Economist, more than 800 million records, such as credit and debit card information, were lost or stolen in 2013. Cybercrime and online industrial espionage costs the global economy $445 billion per year.3
These statistics do not include connected refrigerators, thermostats or other unsuspecting appliances, but in the future, they will. “There have already been instances of nefarious types taking control of webcams, televisions and even a fridge, which was roped into a network of computers pumping out e-mail spam. And security researchers have found ways of hacking into some kinds of medical devices and cars, though this still requires specialist knowledge and kit.”4
On top of traditional cybercrime, the kind of attacks we may see in the future will change with emerging technology. For example, devices placed in remote locations to monitor weather or geographical conditions could become new targets. Cyber attackers might try to get unauthorized access to devices left out in the field, or organize denial of service (DoS) attacks against devices with the intention of reducing their battery life, rendering them useless. More connected devices means more open ports, and therefore more exposure to networks—giving companies and users increased exposure to threats.
Also, IoT products are designed and created using a variety of technologies, which makes it extremely difficult to solve security problems simply by patching firmware (think of every time you update your laptop or smart phone—now multiply that by 10). There are thousands of manufacturers building new sensors, monitors and smart devices using hardware from unknown (or at least hard-to-track) vendors, which increases exposure to other threats.
The incremental number of connected devices creates higher levels of complexity for managing those same products. From a business perspective, it is extremely difficult to secure each and every device on a network. On the web, for example, security has been established through certificates that can be updated or revoked. In an IoT world, certificate management—an already difficult task—becomes a titanic endeavour. According to ZDNet, the challenge “won’t be only security; it’s how do you manage the lifecycle, and then how do you manage your diagnostics.”5
As a result, the traditional approach to cyber attacks—including the release of patches to fix software code—might prove useless in this new scenario.
Something old and something new
If security in the IoT cannot occur at the device level, it is possible that the solution is at the network level—protecting the connection so businesses won’t need to protect the devices. However, there are already some challenges in this approach.
Although the IoT seems like an entirely new market, in reality it’s more of a combination of old and new technologies, which has a large impact on security. According to Gartner, “Each use case risk profile has specific requirements that may result in the use of old platform and service architecture with a new technology ‘overlay’ to improve performance and control.”6 This characteristic of IoT means that security will be built by merging existing and recently developed methodologies.
Securing networks has become more urgent than ever. Networks are usually considered weak points in the architecture of the web, and old problems are resurfacing thanks to increasing number of connected devices. For example, IPv4 (the Internet protocol that conducts more than 90% of Internet traffic) is close to exhaustion. The new protocol currently in development, IPv6, will provide more IP addresses to allow more connected devices, but the implementation has presented some troubles. “With IPv6, there are still a lot of holes that hackers will discover over time [and] once hackers sink their teeth into it, they’ll probably find a lot more things that could potentially go wrong,” Aviv Abramovich, engineering manager at Check Point Software Technologies, explained on ZDNet.7 Some vulnerabilities and issues that were removed from IPv4 have reappeared in the deployment of IPv6.
Organizing a new Internet
The security risks of the IoT have resulted in a series of vendors, working groups and academics pushing for new standards in machine-to-machine (M2M) communications. Effectively, connecting things to the Internet can be accomplished with the help of various protocols and standards, either adopted from the traditional Internet and telecommunications fields (such as WiFi, Bluetooth, Ethernet, 3G and LTE), or specifically tailored to meet the constraints of the connected things (ZigBee, Z-Wave, CoAP and so on). Certainly, the specific requirements of different application domains affect the feasibility of certain technologies.8
In practice, though, it is hard to evaluate the effectiveness of standards, especially considering that the entire scope of the IoT has not yet been revealed. There are still too many makers and thinkers working, testing and experimenting with small chips (like those using the Raspberry Pi), electrical components and new services to have a clear picture of the entire set of security requirements.
Are we sending privacy to the IT museum?
So what happens to users data in the IoT? If a consumer buys a product, where does the data goes once the device “reads” his/her activities or preferences? How is Google—whose core business is selling advertising—planning to use the information it captures through Nest’s thermostats? How is Apple going to use health data collected through its app store?
In a survey conducted by the Economist and ARM, 60% of respondents agreed that lack of trust and concerns about data privacy are hampering consumer uptake of the IoT.9
Users may not know the capabilities of IoT devices, and there may not be acoustic or visual signs to draw the user’s attention to what the device is doing (for example, smart phones tracking location without alerting users). According to the Pew Research Center, “The realities of this data-drenched world raise substantial concerns about privacy and people’s abilities to control their own lives. If everyday activities are monitored and people are generating informational outputs, the level of profiling and targeting will grow and amplify social, economic, and political struggles.”10
Today, there are a number of privacy concerns surrounding the IoT:11
- Preserving location privacy, where location can be inferred from things associated with people
- Prevention of personal information inference, that is, keeping information individuals would wish to keep private from being inferred through the observation of IoT-related exchanges
- Keeping information as local as possible using decentralized computing and key management
- Protecting real identities through use of soft identities, where the real identity of the user can be used to generate various soft identities for specific applications. Each soft identity can be designed for a specific context or application without revealing unnecessary information, which can lead to privacy breaches
Traditionally, ICT companies have approached innovation from a perspective of “making things happen.” In most cases, entrepreneurs (and makers) design and develop products without incorporating security and privacy concerns until late in the process. The traditional approach is to find the user’s “point of tolerance”—people will use a technology as long as the perceived benefits are greater than the risks.
Privacy by Design
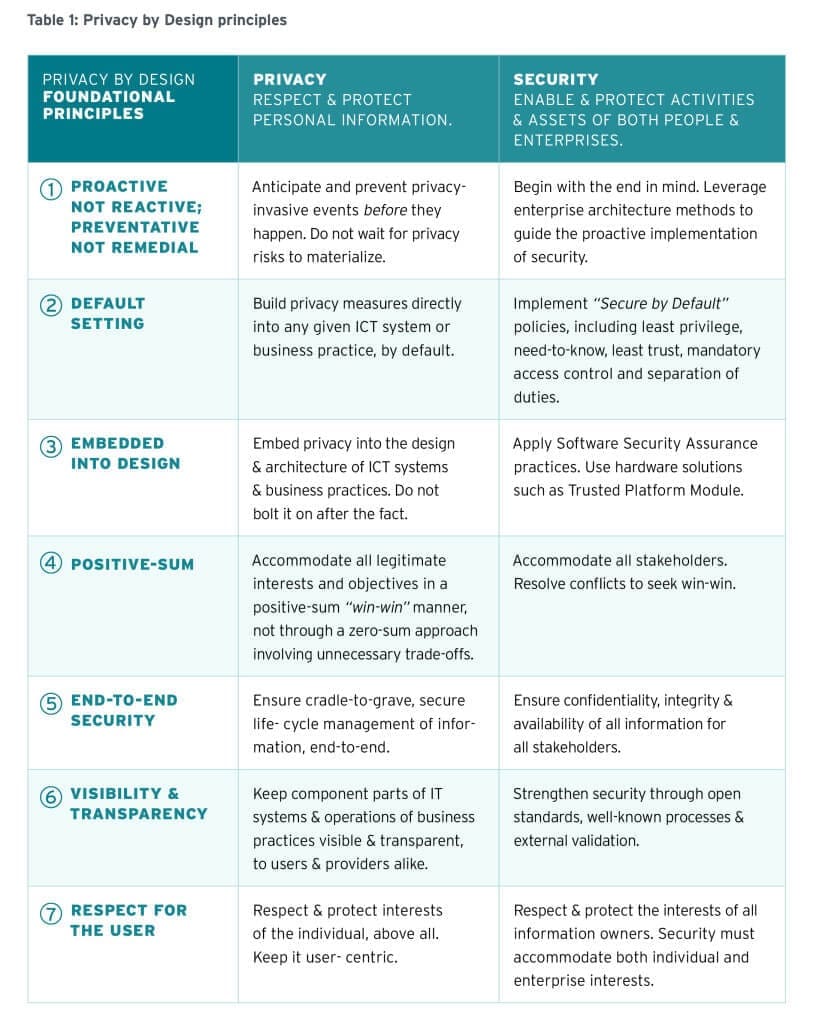
Privacy by Design has existed in Ontario since the late 1990s, and involves the idea of incorporating the understanding of privacy issues into the entire development of new products or initiatives. According to Ann Cavoukian, former Information and Privacy Commissioner for Ontario, “Rather than using the lens of zero-sum trade-offs, we must look at privacy and technology through the lens of positive-sum, mutually beneficial interactions. Like security, privacy need not diminish the functionality of technology. Rather, once properly understood and implemented, privacy works in conjunction with technology and enhances its functionality insofar as it increases end-user satisfaction, consumer confidence, trust and use. Technology is not hindered by privacy, but rather, made far better by it.”12
Figure 1: The foundational principles of Privacy by Design, from Privacy and Security by Design: An Enterprise Architecture Approach, 2013
Frameworks like Privacy by Design are not necessarily new in the world of software design. Traditionally, designers have considered privacy and user safety as main constraints for product development.
The design of connected, safe, and secure things
Most of the makers building IoT prototypes and the entrepreneurs outsourcing their code to third parties do not necessarily rank privacy and security high in their product or business development strategies. Security consultants are not traditional members of a startup’s staff or supporting relationships, unless the product requires higher levels of security to appeal to customers. Financial apps, for example, require high levels of security and privacy; otherwise users would not trust them and would be more likely to reject them. In most other cases, though, security tends to be an afterthought.
The IoT will have a great impact on security strategies and practices. As Gartner points out, “IoT security requirements will reshape and expand over half of all global enterprise IT security programs by 2020 due to changes in supported platform and service scale, diversity and function.”13 As we have seen here, it is not yet clear what challenges the IoT will create in terms of privacy and security, or what challenges companies (including startups) might face. But one thing is definite: Businesses need to scale security governance to deal with all the sensors, monitoring systems and M2M communication devices that will join the ecosystem.
Despite IoT unknowns, today it is possible to start creating products that would satisfy minimum levels of security—or the type of basic security we have learned from developing the web. In a presentation at the Amsterdam GOTO Conference in June 2014, Mark Stanislav, Security Project Manager at Duo Security, presented some basic rules for creating secure IoT solutions.
Ten tips for more secure IoT development:14
- Do not hide sensitive data in your firmware or mobile apps
- Utilize a platform that supports auto-update functionality
- If it goes over a network, it almost certainly should be encrypted
- Verify API requests (for example, HMAC signature), even with SSL transport
- Encrypt and segment customers’ data from one another at rest
- Research chipsets you buy from an original design manufacturer (ODM) for known issues
- Use bcrypt/scrypt/PBKDF2 for one-way data storage
- Automate tests to verify data is only accessible when expected
- Work with reputable vendors and don’t trust their security, either
- Data outside of your server is no longer trustworthy data
Regarding established organizations, there are also some guidelines to deploying IoT solutions. Gartner has published a quick framework to deal with the challenging security issues of the IoT. The research company recommends:
- Deconstructing current principles of IT security in the enterprise and expanding security planning to include new and old technology and service delivery
- Evaluating incoming IoT security requirements that account for possible combinations of mainframe, client/server, web, cloud and mobile security needs, which are impacted by operational technology (OT) and physical security in specific use cases’
- Developing “initial IoT security projects based on specific, even tactical, business risk profiles, then build on those experiences to develop common security deployment scenarios, core architectural foundations and responsibilities”15
Thinking about the design of new things
The conversation around security in an IoT era is permeating other professional fields. In April 2014, a group of designers got together in downtown Toronto for a discussion about the Programmable World. Matt Nish-Lapidus, Design Director at Normative (a design shop in Toronto), opened the evening discussion with a short presentation introducing the idea that we live surrounded by a network of machines that tracks everything. He argued that this network is making “design decisions,” in the sense that some interactions are hidden from users and therefore the users can’t take action to control the flow of information.
“We put stuff into the world but we don’t really think about its impact. And we help create a certain culture around it,” he said.
Startups tend to create products and business models first, and think of the impact of those creations later. And users, traditionally, have willingly accepted trade-offs regarding privacy or security when the perceived benefit of using a particular product is bigger than the perceived risk. In this sense, the IoT might offer us a great opportunity.
Many of the effects of living in a world where everything is connected are still unknown. It is not clear what type of solutions consumers will find appealing, what business cases will make sense to organizations, and what startups will survive ideation stages. As we have seen throughout the Connected World series reports, a number of startups are working on new solutions that require high standards of security and privacy to be successful, such as health or weather monitors. In those cases, the design of these M2M-powered solutions will require a new layer of trust
Users will probably feel more inclined to adopt technologies that do not put their safety or security at risk. Certainly, embedded security for heart monitors is an essential requirement that users will demand before adopting new technologies. But we can argue that security for other type of products can also provide the edge a startup might need to distinguish in the market. For example, after Edward Snowden argued that Dropbox was “hostile to privacy”, Spider Oak , a competing company, saw huge spikes of visitors and sign ups16 a sign that users do care about privacy and security.
Similarly, users will not appreciate waiting for crucial updates—for example, to the system that will help them avoid an insulin overdose or to the monitor that controls their home’s chimney, which might keep the house from burning down.
These examples, the type of solutions that require embedded security and privacy might offer a great starting point to analyze and identify the new security and privacy requirements of the physical web, and also offer a glimpse into the market-driven security of tomorrow.
References
1. Forrester. (2013). Prepare I&O For The “Internet Of Things.” Retrieved from http://www.forrester.com/Prepare+IO+For+The+Internet+Of+Things/fulltext/-/E-RES93301
2. Gartner. (2013). Gartner Says the Internet of Things Installed Base Will Grow to 26 Billion Units By 2020 Retrieved from http://www.gartner.com/newsroom/id/2636073
3. No author. (July 12, 2014). The Internet of things (to be hacked). The Economist. Retrieved from http://www.economist.com/news/leaders/21606829-hooking-up-gadgets-web-promises-huge-benefits-security-must-not-be
4. The Internet of things (to be hacked). The Economist.
5. Lee, M. (2013). M2M and the Internet of Things: How secure is it? ZDNet. Retrieved from http://www.zdnet.com/m2m-and-the-Internet-of-things-how-secure-is-it-7000008389/
6. Gartner. (2014). What securing the Internet of Things means for CISOs. Retrieved from https://www.gartner.com/doc/2706521/securing-internet-things-means-cisos
7. M2M and the Internet of Things: How secure is it? ZDNet.
8. Mazhelis, O.; Warma, H.; et al. (2013.) Internet-of-Things Market, Value Networks, and Business Models: State of the Art Report. University of Jyväskylä. Retrieved from http://www.internetofthings.fi/file_attachment/get/IoT%20SOTA%20Report%202013.pdf?attachment_id=9
9. Witchalls, C. (2013). The Internet of Things business index. The Economist. Retrieved from http://www.economistinsights.com/analysis/internet-things-business-index
10. Anderson, J.; Rainie, L. (2014). The Internet of Things Will Thrive by 2025. Pew Research. Retrieved from http://www.pewInternet.org/2014/05/14/Internet-of-things/
11. Vermesan O and Friess P (editors). (2013). Internet of Things: Converging Technologies for Smart Environments and Integrated Ecosystems.
12. Cavoukian, A.; Dixon, M. (2013). Privacy and Security by Design: An Enterprise Architecture Approach. Retrieved from http://www.privacybydesign.ca/index.php/paper/privacy-security-design-enterprise-architecture-approach/
13. Gartner. What securing the Internet of Things means for CISOs.
14. Stanislav, M. (2014). How we’re failing to secure the “Internet of Things.” Speaking notes. Retrieved from https://speakerdeck.com/mstanislav
15. Gartner. What securing the Internet of Things means for CISOs.
16. Kim E (2014) Edward Snowden Wants You To Ditch Dropbox For This Service. Business Insider. Available at http://www.businessinsider.com/edward-snowden-dropbox-2014-7
The Connected World Market Insights Series
The Connected World Market Insights Series will cover such topics as:
- Advanced metering infrastructure (AMI) and smart meters: Building upon a home advantage
- Automation and energy: Unlocking home and building energy management opportunities
- Entertainment for the connected home
- Security: Privacy, data ownership and data risk
- Transforming health: Decentralized and connected care
- Connected mining opportunities and new technologies
- The value of real-time meter data
Accessing data is key, but we think that being able to format and analyze that data is where the real value can be found. During this series, MI will delve into the market opportunity now becoming available due to progress in opening up datasets, and the development of infrastructure and analytics that are creating new services and products and bringing them to market.